-
Leading organizations embrace information security from the top down, and employees are given the right resources to defend against a breach.
August 21 -
Researchers have seen at least three cyber espionage operations using this technique, says Alexey Shulmin of Kapersky Lab.
August 8 -
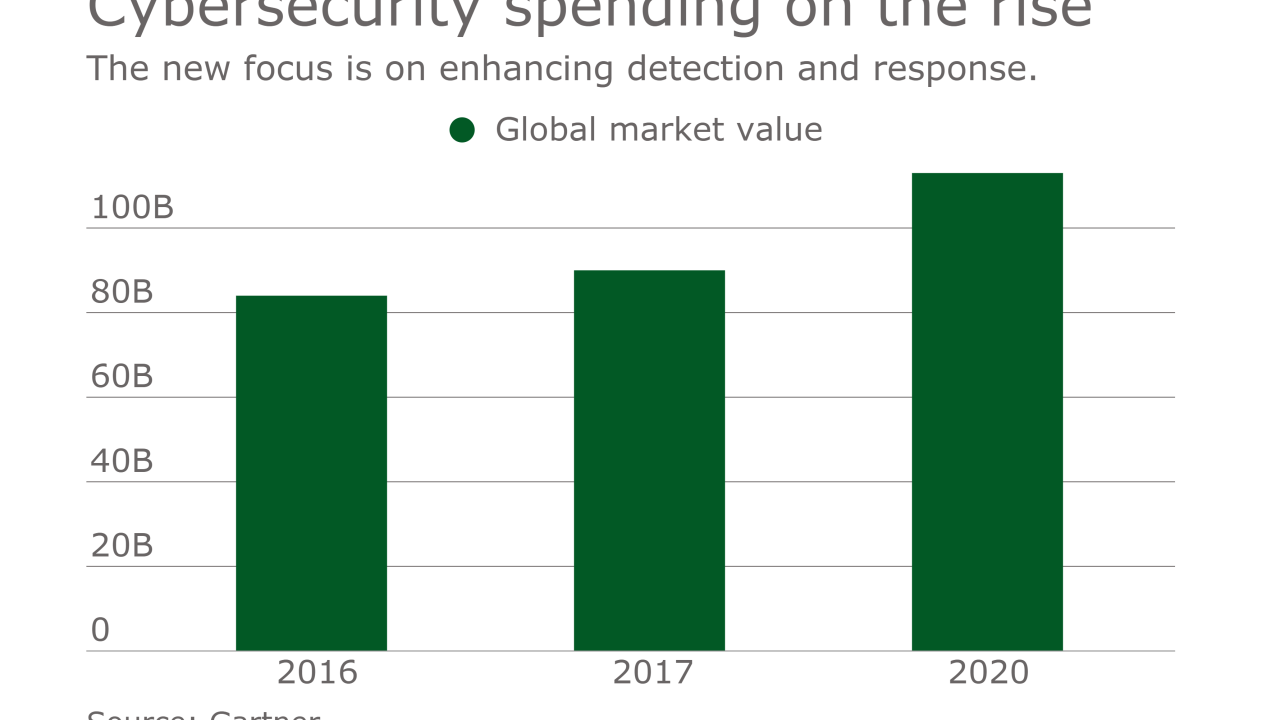
The need is for EDR, software-defined segmentation, cloud security, and user and entity behavior analytics.
March 16
Load More